Preventing Scope Downgrades in OAuth Flows
Introduction
When implementing OAuth flows, ensuring that user permissions (scopes) are correctly managed is crucial. A subtle bug can lead to unintended scope downgrades, limiting the application's access to necessary resources. This post discusses a fix in the devlog-ist/landing project to prevent such downgrades during GitHub login.
The Problem
The devlog-ist/landing project encountered an issue where the GitHub login process inadvertently overwrote existing user scopes. Specifically, if a user had previously granted access to private repositories (via the github_private_access scope), subsequent logins through the standard login page would overwrite this with the public_repo scope. This occurred because the login page didn't explicitly request github_private_access, leading to an OAuth redirect that only requested public_repo scope.
On the OAuth callback, the existing user's github_scope was then overwritten, effectively revoking access to private repositories. This was a significant problem, as it silently reduced the application's functionality for affected users.
The Solution: Preserving Existing Scopes
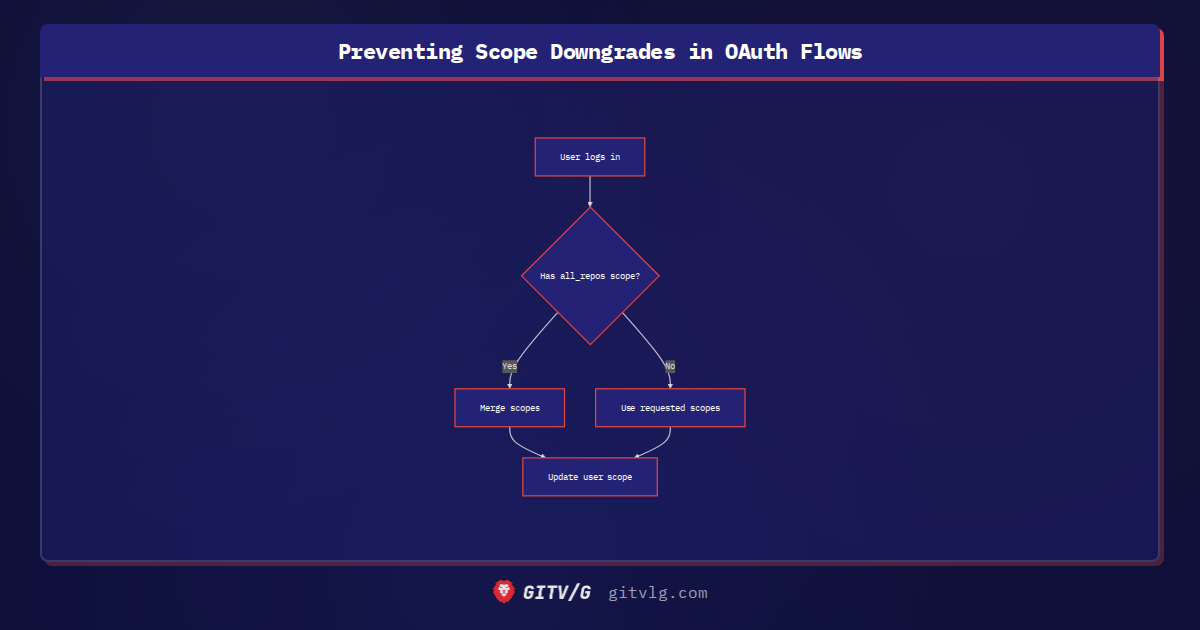
To address this, a change was implemented in the resolveEffectiveScope() function. The updated logic now preserves the AllRepos scope (representing access to all repositories) when it already exists for a user. This prevents scope downgrades during login while still allowing for scope upgrades if new permissions are explicitly requested.
Here's a simplified example of how the resolveEffectiveScope() function might work:
function resolveEffectiveScope(array $existingScopes, array $requestedScopes): array
{
$allReposScopeExists = in_array('all_repos', $existingScopes);
if ($allReposScopeExists) {
// Preserve all_repos scope if it already exists
return array_unique(array_merge($existingScopes, $requestedScopes));
} else {
// Otherwise, use the requested scopes
return $requestedScopes;
}
}
In this example, if the $existingScopes array already contains all_repos, the function merges the existing and requested scopes while ensuring uniqueness. Otherwise, it defaults to using only the $requestedScopes.
Benefits
- Prevents unintended scope downgrades: Users retain access to previously granted permissions.
- Maintains application functionality: Ensures the application can continue to access necessary resources.
- Improves user experience: Avoids silent permission revocations that can lead to unexpected behavior.
Conclusion
Properly managing OAuth scopes is crucial for maintaining the integrity and functionality of applications. By preserving existing scopes during the login process, the devlog-ist/landing project prevents unintended permission downgrades and ensures a consistent user experience. When implementing OAuth flows, always consider the potential for scope overwrites and implement safeguards to protect existing user permissions. Review your OAuth implementation to ensure existing scopes are preserved during re-authorization flows.